Lokibot Campaign
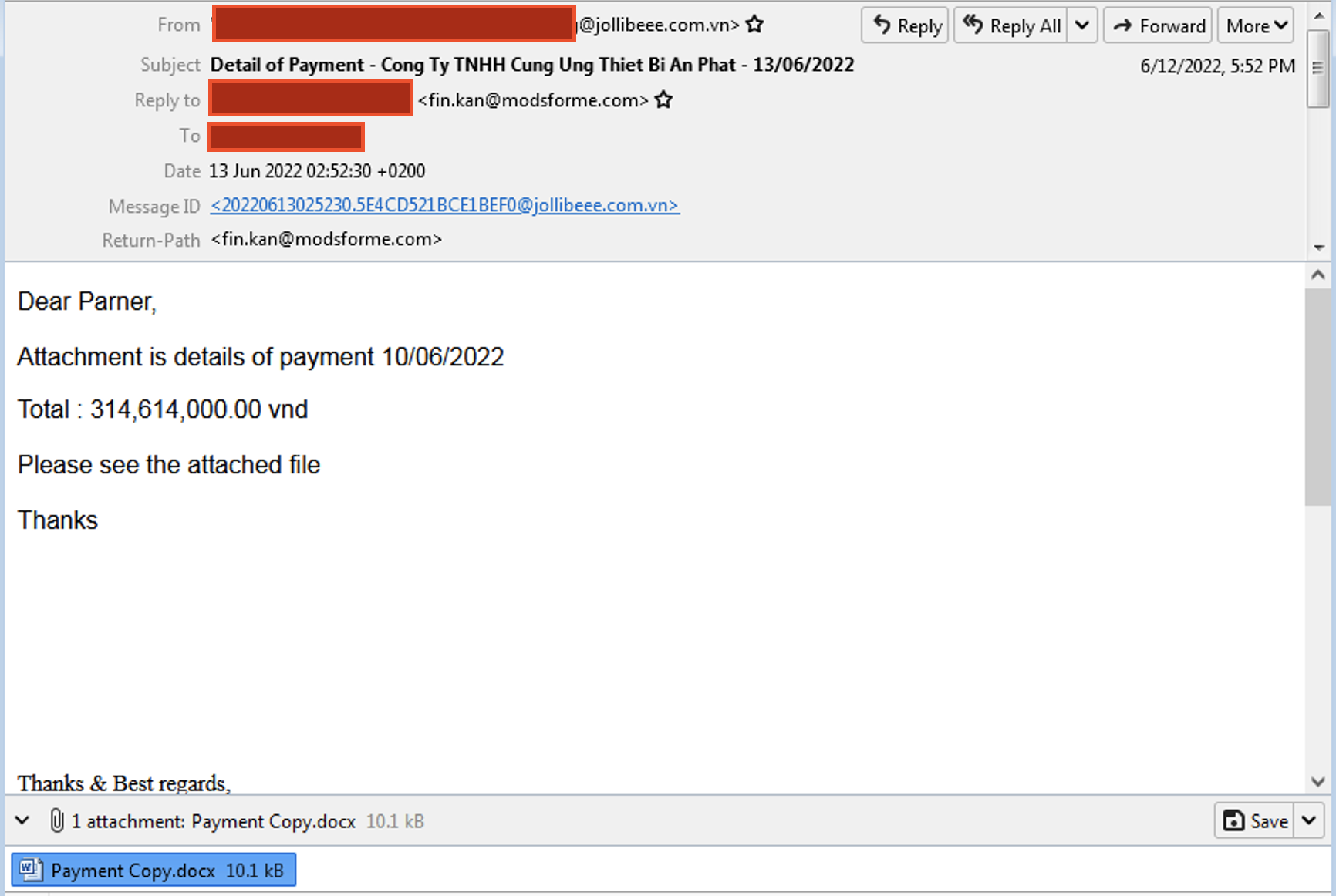
Disclaimer: Opinions expressed are solely my own. None of the ideas expressed in this blog post are shared, supported, or endorsed in any manner by my employer. In this blog, we take a look at Lokibot campaign. The email MD5: a42ef269e70416810810d0fa01fe02ee SHA256: 8f8bc761f92ff8f3c442699c8b41358e5716339482264f1ef7d09eb57f68b9f0 VT: https://www.virustotal.com/gui/file/8f8bc761f92ff8f3c442699c8b41358e5716339482264f1ef7d09eb57f68b9f0 The campaign begins with a email. The Email Sample The email has a different email-id in From and Reply-to header. It contains an attachment named "Payment Copy.docx" . It appears to be sent from 45.143.7.113 Geolocation information of IP The Attachment MD5: 1ba139d79438fc4406ab8b8fd93f6a30 SHA256: 94fa80c133c152abe46e0f6f20c06b1f27c225f2723915596af2ad8499fa4ff0 The attachment is a docx file which can be treated as a zip file. After unzipping, we check the file word/_rels/webSettings.xml.rels w...