Loading GootLoader
Disclaimer: Opinions expressed are solely my own. None of the ideas expressed in this blog post are shared, supported, or endorsed in any manner by my employer.
In this blog, I will be taking a look at the initial GootLoader sample (MD5: 4dd369b5e028beebe3aa5c980960c502 , Sha256: c1029f0b5f4f6dfbe0fe656f075cbb5ccc2fc308087db21438d73394b75ea020).
Available here: https://bazaar.abuse.ch/sample/c1029f0b5f4f6dfbe0fe656f075cbb5ccc2fc308087db21438d73394b75ea020/
The sample is a javascript program which is meant to be executed in windows using wscript.exe.
Opening the sample in a text editor, it appears to look like jquery library 3.6.0 (screenshot below).
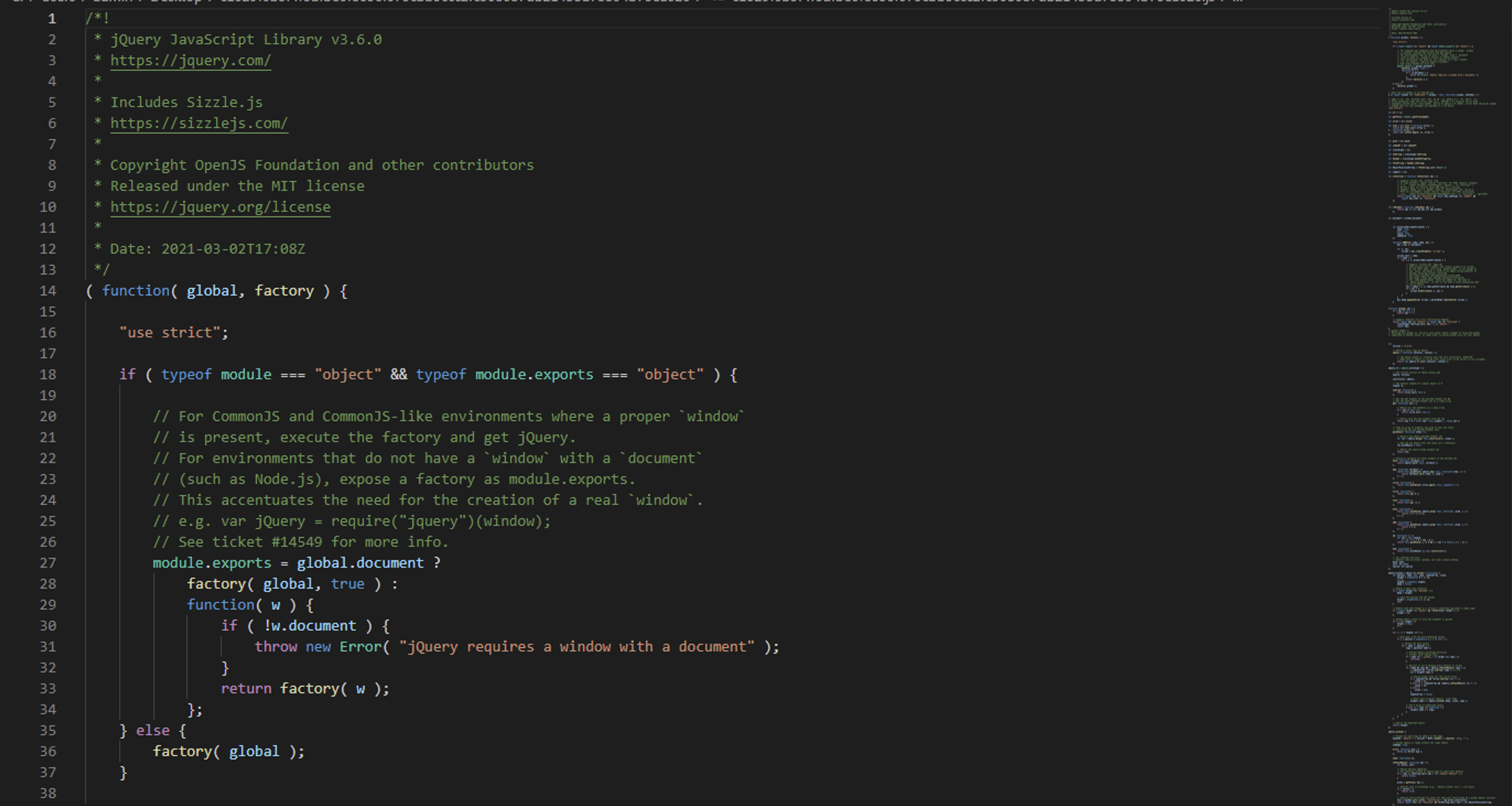 |
One important thing to mention about javascript: If a variable is declared without keywords such as var, it will be treated as global variable.
After reading the code, following points can be observed:
- Function seat07() is incrementing a variable in a loop. The incremented variable is not referred in any part of the code. This is most likely done to increase the execution time and thus timeout sandbox detection. Commenting out the function would speed up the execution.
- Function gone068() contains the obfuscated string which is likely deobfuscated and executed. Generally, deobfuscated string would require one of the following to be executed:
- eval()
- function constructor
- window object
- It would be interesting to see how deobfuscated string is executed in this sample.
- Function law1() and present4() are quite interesting because they are accessing array elements and making a call. They could be used to call deobfuscating routine and execute the deobfuscated string.
- Deobfuscated strings are executed using function constructor.
- It contains obfuscated string which needs to be deobfuscated.
- It also seems to be accessing the registry: HKEY_CURRENT_USER
- It checks if the environment variable userdnsdomain is set which would indicate that the system is part of AD.
- If active directory is set, then it would add the string "4173581" to parameter value in its requests.
- The C2 communication would look something like this:
- GET request to server with path: test.php?zgntopmtyplqx=
- The parameter will be <random value>4173581 if computer is part of AD otherwise only <random value>
- If the http response status code is anything other than 200, it would sleep for 12345 milliseconds and check for another domain.
- If the http response status code is 200, then it would look for the string : "@<parameter value sent>@" in the response text.
- if it is not present, then it will sleep for 23232 milliseconds.
- If it is present, then it will do the following:
- Remove the string "@<parameter value sent>@" in the response text.
- Response text is likely to be series of numbers which are parsed as integers then converted to ascii strings which are then deobfuscated.
- https://news.sophos.com/en-us/2021/03/01/gootloader-expands-its-payload-delivery-options/
- https://thedfirreport.com/2022/05/09/seo-poisoning-a-gootloader-story/
Comments
Post a Comment