Lokibot Campaign
Disclaimer: Opinions expressed are solely my own. None of the ideas expressed in this blog post are shared, supported, or endorsed in any manner by my employer.
In this blog, we take a look at Lokibot campaign.
The email
MD5: a42ef269e70416810810d0fa01fe02ee
SHA256: 8f8bc761f92ff8f3c442699c8b41358e5716339482264f1ef7d09eb57f68b9f0
VT: https://www.virustotal.com/gui/file/8f8bc761f92ff8f3c442699c8b41358e5716339482264f1ef7d09eb57f68b9f0
The campaign begins with a email.
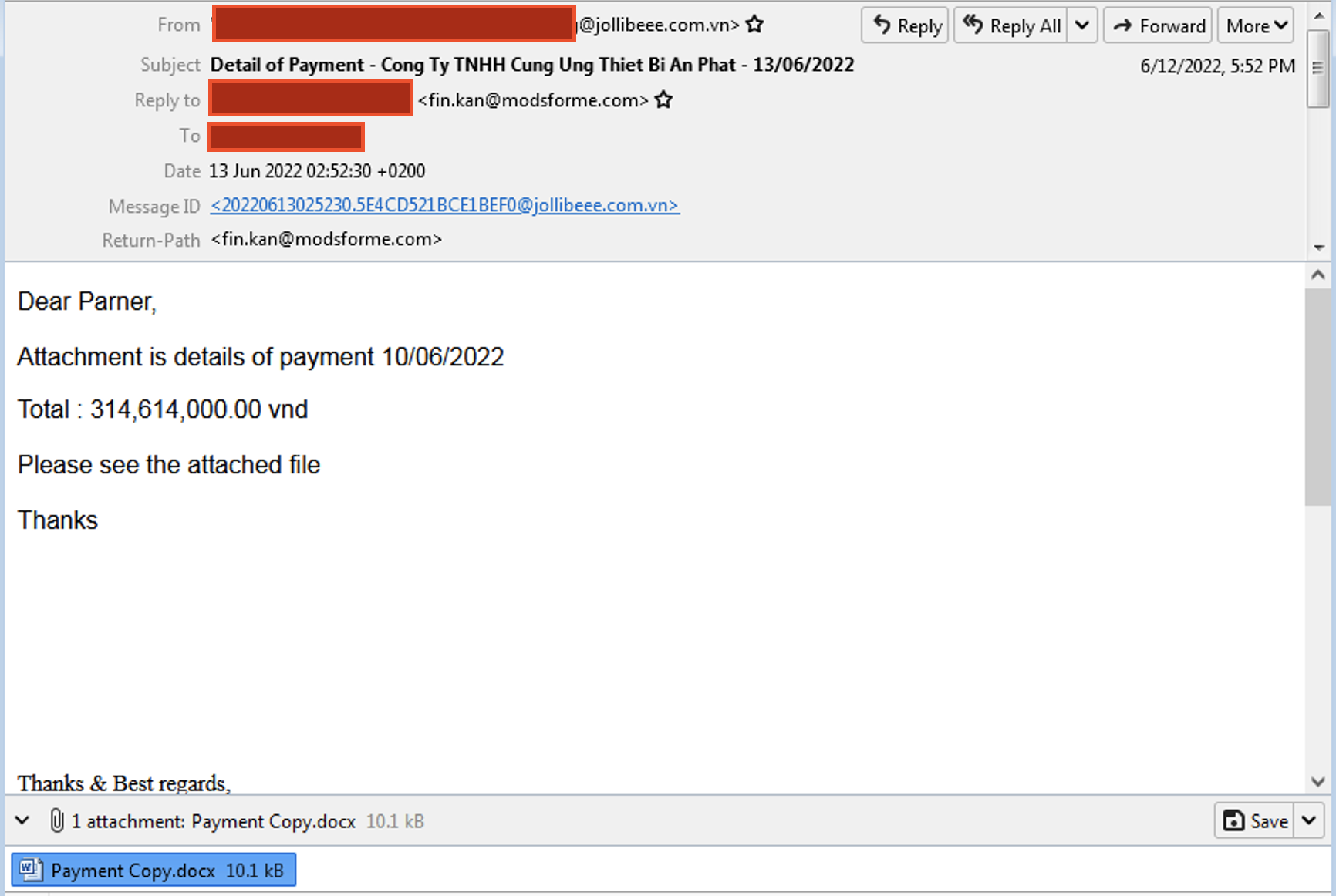 |
| The Email Sample |
The email has a different email-id in From and Reply-to header. It contains an attachment named "Payment Copy.docx" . It appears to be sent from 45.143.7.113
 |
| Geolocation information of IP |
The Attachment
MD5: 1ba139d79438fc4406ab8b8fd93f6a30
SHA256: 94fa80c133c152abe46e0f6f20c06b1f27c225f2723915596af2ad8499fa4ff0
The attachment is a docx file which can be treated as a zip file.
After unzipping, we check the file word/_rels/webSettings.xml.rels where we see the remote url
Ref: https://www.virustotal.com/gui/url/05a382cf2cf7034327f962639d4568a0e32686213cc81b5b00c29680f229aaa0/
The RTF File
MD5: e863c296b56a2186b662b7cce8e4aaa5
SHA256: db46ba6c7bccd43b5a5ecb729ef23dfa58fbcd8ee7720a15696f33ace895522f
The file downloaded is named as invoice.doc which is a RTF file.
Using rtfdump.py, we see the following streams:
 |
| Output of the RTFDump tool |
 |
| Highlighted CLSID of Equation Editor |
Also, we see an OLE10 native stream in it which typically contains a shellcode.
Shellcode
After dumping the OLE10 native stream, we use scdbg to find the shellcode:
 |
| Output from shellcode emulation |
The shellcode downloads a file from the url: hxxp://103[.]207[.]39[.]127/http/csrss[.]exe to the path: C:\Users\Public\vbc.exe and executes it.
The url downloads a .NET file. Ref: https://www.virustotal.com/gui/url/3196722e5834a7384895967a3518ad5d1a6830d85586ba6a6508f59c949b4b47
The .NET loader
MD5: 80ca5fbabeb4b62af4beb588c3b2f9e1
SHA256: 79ece3edc65e0f2110c5f126bd0ea4e3cd8ca1ca4a3c8f747580b2fd010105ad
The .NET file contains fake information such as:
The file has a high entropy: 7.795. In the resource section of .Net , we see a png image named EncoderFallb with an entropy of 7.99663 and a file named Converter with an entropy of 7.84998:
The file initially deobfuscates and loads the Converter resource in the memory which is a dll file named ArgIteratorZAA :
First DLL loaded in memory
MD5: 79c5c39e29ebe233cd13a50987e64609
SHA256:dec15271d422cf3b82c0a94cf147312bb5a4a4f262da4b698ffe7e6bdaf18053
The class ArgIterator is invoked with 3 parameters: "456E636F64657246616C6C62" (EncoderFallb) , "4762623247675155" (Gbb2GgQU) , "MusicGenerator" . In the below figure, we see the function accepting these 3 arguments:
It first sleeps for 41263 milliseconds. Then it extracts another dll file (TweenEngineAPI.dll ) from the EncoderFallb resource of the initial .NET file, deobfuscates and loads in it the memory.
 |
| Extraction of EncoderFallb resource |
Second DLL loaded in memory
MD5: 31a462b762d57132485a38cc29c33a6c
SHA256: 52aeeb77b743fc532b8d00d2fe039f0c33e01555dc0ed7a89c1e6e4141016218
TweenEngineAPI.dll file contains a lot of classes which are not used. It contains 2 resources:
- hElOI3eyMgU3Ua5HeM.yiCiaCyuKn7k930nYn
- JLCOcB0OitZkA6cLMR.7lqMfmnIZVJv8pPoJh
 |
| List of resources and classes (cut for brevity) |
This dll starts its execution from the class: u5deZApOUp1We7GkZP where it performs the following actions:
- It first extracts its own resources: hElOI3eyMgU3Ua5HeM.yiCiaCyuKn7k930nYn and JLCOcB0OitZkA6cLMR.7lqMfmnIZVJv8pPoJh which is deobfuscated and loaded in the memory.
- The file loaded in the memory is a dll file named: a9551989-c0ed-4d71-8e51-a6bc3e7a51a4.dll
Third DLL loaded in memory
MD5: 741d92a5d66a22ac24ead7beefd8752e
SHA256: 5d83b0bc6bf2ededa11662b5c43e64cdbfbf01c33733ab3c1546978276f2d782
This dll doesn't contain any code. It contains 3 resources. Out of these 3 resources, XK83TbKgcF is the resource which is extracted by the TweenEngineAPI.dll, previously loaded DLL file.
TweenEngineAPI.dll (second in-memory loaded) file does the following after extracting the resource (XK83TbKgcF) from a9551989-c0ed-4d71-8e51-a6bc3e7a51a4.dll :
- The extracted resource is deobfuscated which is the lokibot stealer sample.
- It dynamically resolves the following APIs:
- "ResumeThread"
- "Wow64SetThreadContext"
- "SetThreadContext"
- "Wow64GetThreadContext"
- "GetThreadContext"
- "VirtualAllocEx"
- "WriteProcessMemory"
- "ReadProcessMemory"
- "ZwUnmapViewOfSection"
- "CreateProcessA"
- The above APIs are typically used for process hollowing. In this case, it spawns a new process of itself and uses process hollowing to write the extracted lokibot sample into it.
The Lokibot Sample
MD5: 28a1ba29828935a65c660d30e64c0c5f
SHA256: 06d16c53db8da86d86cc9b91ba511fd5a04f7e40f41b1bfcaaa1929e201157b9
ssdeep:"1536:czvQSZpGS4/31A6mQgL2eYCGDwRcMkVQd8YhY0/EqfIzmd:nSHIG6mQwGmfOQd8YhY0/EqUG"
The lokibot sample performs the following actions described in https://malpedia.caad.fkie.fraunhofer.de/details/win.lokipws
Currently, C2 server (sempersim.su) is down. The url contacted is: hxxp://sempersim[.]su/gh5/fre.php
Once the lokibot is executed, the .net loader file deletes itself from the disk.
Extra:
In this analysis, Dnspy's modules and module breakpoint was used to dump the in-memory loaded file. Refer this video for more advance reversing tricks in Dnspy: https://www.youtube.com/watch?v=yxw4h82mQ2s
You can also use the tool DotDumper unveiled at Blackhat this year. The tool is available at https://github.com/advanced-threat-research/DotDumper. You can read more here: https://www.trellix.com/en-hk/about/newsroom/stories/threat-labs/dotdumper-automatically-unpacking-dotnet-based-malware.html
By using DotDumper tool, you can automatically dump all the 3 dll files and read the logs to check the call trace and perform further analysis. However, the final Lokibot sample is not dumped since it is not loaded in the memory but instead written into another process in this case.
Thanks for Reading. Have a Good Day!







Comments
Post a Comment